'Among various encryption technologies that provide privacy, the Zero-Knowledge Proof is one of the most important technologies', Sin7Y_Labs.
Privacy has always been regarded as one of the most valuable features in the cryptocurrency community as most crypto-asset holders do not want their assets and transaction records to be fully disclosed. Among various encryption technologies that provide privacy, the Zero-Knowledge Proof is one of the most important technologies.
The Zero-Knowledge Proof is essentially a protocol involving two or more parties, which is a series of steps that two or more parties need to take to complete a task. Is there any way to prove that A knows where the panda is without letting anyone else know the answer?Then, A cuts a small hole in the white paper to expose the panda only.
The proof difficulty is to make the proof more difficult mathematically directly; the interaction degree means that the verifier needs to constantly ask the prover questions, and then the prover proves that it is more difficult for the prover to deceive the verifier as the number of their interactions increase because the probability of the prover providing the correct proof without knowing the correct information decreases statistically.
In the following ten years, many legendary cryptographers have made important contributions to the development of the Zero-Knowledge Proof systems. In 2010, Jens Groth proposed the Knowledge of Exponent Assumption, which was controversial at that time. It has shortened the proof length to a constant level by hiding some secret random values in CRS.
In 2013, Rosario Gennaro, Craig Gentry, and others made a more optimized improvement solution based on the work of Jens Groth in 2010, which has greatly shortened the proof time and reduced the proof length to a smaller constant. At present, there are mainly the following solutions for Zero-Knowledge Proof. Each solution represents different Zero-Knowledge Proof practices, which will also produce different effects,The horizontal axis is proof size, while the vertical is security assumptions. Among them,which does not rely on mathematical difficulties assumptions and has a postquantum character.
**Currently, Groth16 is the zk-SNARK with the fastest verification speed and smallest data size, and Zcash is its first widely spread implementation. Groth16 is a further refinement of the Pinocchio protocol, compressing the proof size by nearly half with slightly stronger security assumptions. To solve this problem, Stanford cryptographers Benedikt Bünz and others proposed Bulletproof technology. Compared with prior zk-SNARK, there is no need to initialize trusted settings for Bulletproof, but it takes longer to compute and verify than STARK with a much smaller proof size. Once proposed, this solution was adopted by the Monero Project.STARK is short for Scalable Transparent Argument of Knowledge. It was established as a substitute version of SNARK.
The security of a trusted setting Zero-Knowledge Proof system can be largely attributed to the security of common references generation. It is possible to realize centralization generation in a trusted manner while incompatible with the goal of decentralization.The MPC solution attempts to ensure that no party could generate or acquire knowledge of the underlying mathematical structure of these parameters.
“Updatable” here means that the trusted settings can be updated at any time as long as a secret is suspected of having been compromised. Although blockchain has always advocated anonymity, participants do not need to use their real names in most transactions, while they can still repeatedly use public key hash values as transaction identifiers to identify the traders.
Zcash wallet address is divided into hidden address and transparent address.
The processing scale of a single shard is small, and even only part of the network state is stored. But, in theory, the throughput of the whole network will be improved under the condition of multiple shards processing transactions in parallel. However, such an approach will lead to the sacrifice of decentralization;
Rollup refers to performing complex off-chain computing and state maintenance first, then conducting on-chain saving for the data related to a state change in the way of calling it through contract by using the cheaper CALLDATA, by which summarizing and packaging a large number of transactions into one transaction, and finally improving TPS on the premise of ensuring [data availability].
Only after passing the verification can the state be changed. That is, the state change of ZK Rollup depends strictly on the cryptographic proof. However, the cost of each transaction is lower, and the verification cost is much lower than the computing cost. Such simplicity provides conditions for scaling.
Current applications can be roughly divided into the following three categories. In this section, we will introduce some very promising Zero-Knowledge Proof projects, most of which have not yet issued tokens.Once with a name called Coda Protocol, the Mina was founded in 2017. Its development team is O Labs, which is composed of world-class cryptographers, engineers, PhDs, and entrepreneurs now.
The node only needs to verify the proof, so it does not need to detect the whole transaction history. It can also cooperate with other public chains through a transfer bridge, enhancing the interoperability and making the entire blockchain ecosystem mutually beneficial and win-win. As well, it is featured lightweight nodes, which are only developed in this field by Mina currently.In March 2022, Mina announced that they had completed a US$92 million strategic financing round led by FTX Venture and Three Arrows Capital.
The SNARK algorithm used by zkSync at the beginning is Groth 16, with which, not only a trusted setting is required , but every new application upgrade on zkSync requires a trusted setting. What is even more remarkable about this round of financing is the introduction of a large number of ecological partners, including some of the most well-known companies and founders in the cryptocurrency field.
StarkWare, like zkSync, has also used the Zero-Knowledge Proof scaling solution, while StarkWare is STARK-based. Three main applications dydx, Immutable, and, Deversifi, are supported by StarkEx. Until now, through these applications, StarkEx has processed over 5 million transactions, with the worth over US$250 billion.
There are two main functions of the Aztec network. One is to protect the interacting privacy of users, and the other is that users can establish total private applications with the programmable privacy contracts provided by Aztec. Based on the current disclosure, the approaching third stage will be Aztec 3.0, to realize the private smart contract of L2 on the Ethereum through the Noir privacy programming language.
In typical public blockchains, the program is executed on-chain in a global “virtual machine” run by each network node. Therefore, every node on the network must recompute each step of the given program, which is inefficient, reduces speed, and increases costs for the users.
France Dernières Nouvelles, France Actualités
Similar News:Vous pouvez également lire des articles d'actualité similaires à celui-ci que nous avons collectés auprès d'autres sources d'information.
 Luna Foundation Guard's Reserve Balance Declines to Zero to Defend UST PegLuna Foundation Guard (LFG) has moved all of its reserves to bitcoin exchanges to defend its UST stablecoin’s 1:1 dollar peg. LFG’s reserve balance has declined from 80,394 BTC to zero, and the majority has been deposited onto the Gemini exchange. 'All About Bitcoin' host Christine Lee breaks down the Chart of the Day.
Luna Foundation Guard's Reserve Balance Declines to Zero to Defend UST PegLuna Foundation Guard (LFG) has moved all of its reserves to bitcoin exchanges to defend its UST stablecoin’s 1:1 dollar peg. LFG’s reserve balance has declined from 80,394 BTC to zero, and the majority has been deposited onto the Gemini exchange. 'All About Bitcoin' host Christine Lee breaks down the Chart of the Day.
Lire la suite »
 Flip Flop-Wearing Designer ID’d as Passenger Who Landed Plane With Zero Experience39-year-old interior designer Darren Harrison wore flip flops as he successfully landed an aircraft despite having zero flying experience.
Flip Flop-Wearing Designer ID’d as Passenger Who Landed Plane With Zero Experience39-year-old interior designer Darren Harrison wore flip flops as he successfully landed an aircraft despite having zero flying experience.
Lire la suite »
 Do the Rich See Inequality As A Zero-Sum Game?California has one of the highest levels of income inequality in the nation, and nearly six out of 10 California adults polled said they believe the government should do more to reduce the gaps between rich and poor.
Do the Rich See Inequality As A Zero-Sum Game?California has one of the highest levels of income inequality in the nation, and nearly six out of 10 California adults polled said they believe the government should do more to reduce the gaps between rich and poor.
Lire la suite »
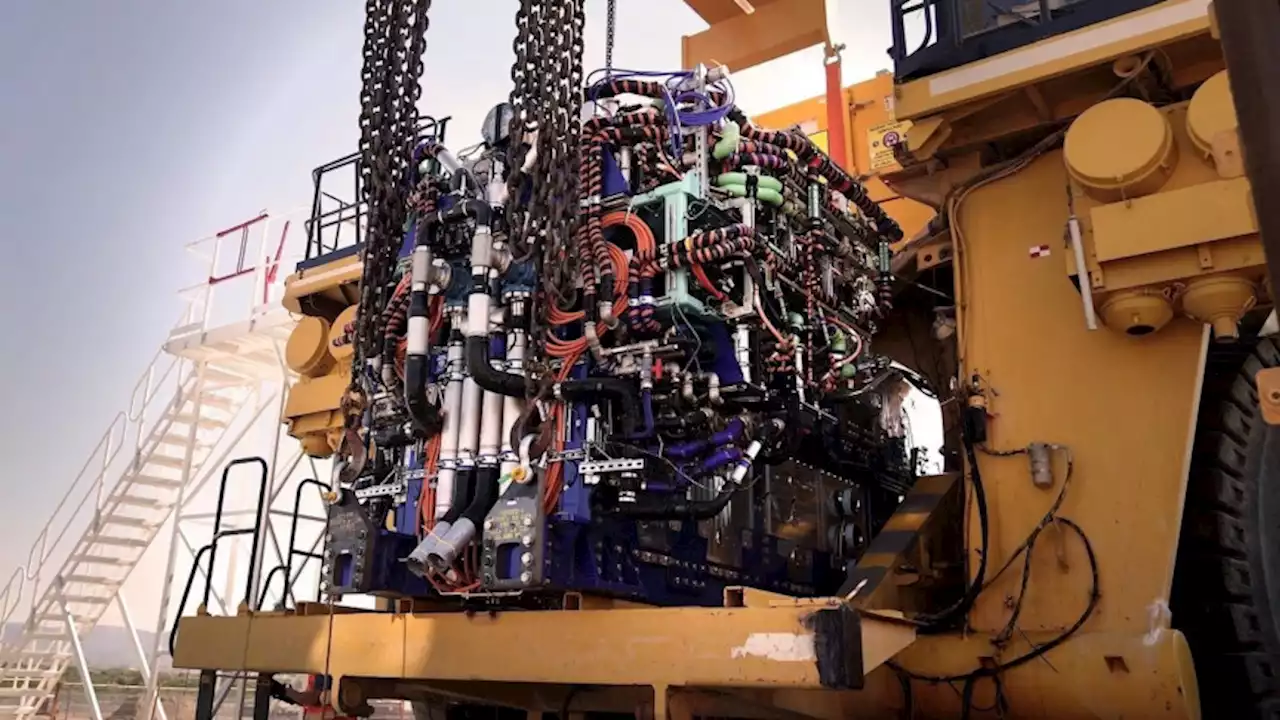 The largest zero-emission vehicle runs on a massive 2-MW hydrogen powerplantIt's part of a company's goal to start decarbonization 'at the source'.
The largest zero-emission vehicle runs on a massive 2-MW hydrogen powerplantIt's part of a company's goal to start decarbonization 'at the source'.
Lire la suite »
 Do the rich see inequality as a zero-sum game?A UC Berkeley inequality study finds that, although efforts to reduce inequality are popular, many of the rich or people in “advantaged groups” resist equity policies, believing they’ll be harmed. Do the rich see inequality as a zero-sum game?
Do the rich see inequality as a zero-sum game?A UC Berkeley inequality study finds that, although efforts to reduce inequality are popular, many of the rich or people in “advantaged groups” resist equity policies, believing they’ll be harmed. Do the rich see inequality as a zero-sum game?
Lire la suite »
 Genshin Impact Developer Reveals New Game Zenless Zone ZeroGenshin Impact developer miHoYo, using the global brand of HoYoverse, has officially revealed its [...]
Genshin Impact Developer Reveals New Game Zenless Zone ZeroGenshin Impact developer miHoYo, using the global brand of HoYoverse, has officially revealed its [...]
Lire la suite »
