Explore how AST parsing, Babelfish UAST, and backward slicing algorithms work together to enforce crypto rules and enhance application security.
Authors: Anna-Katharina Wickert, Technische Universität Darmstadt, Darmstadt, Germany ; Lars Baumgärtner, Technische Universität Darmstadt, Darmstadt, Germany ; Florian Breitfelder, Technische Universität Darmstadt, Darmstadt, Germany ; Mira Mezini, Technische Universität Darmstadt, Darmstadt, Germany . Table of Links Abstract and 1 Introduction 2 Background 3 Design and Implementation of Licma and 3.1 Design 3.2 Implementation 4 Methodology and 4.
is given in Figure 1. First, we parse a source code file into the respective Abstract Syntax Tree . More specifically, we use Babelfish to create a Universal Abstract Syntax Tree which combines language-independent AST elements with language-specific elements. For simplicity, we use the term AST in the remainder of the paper. Second, we apply the
In this section, we describe the design of our static analysis tool is given in Figure 1. First, we parse a source code file into the respective Abstract Syntax Tree . More specifically, we use Babelfish to create a Universal Abstract Syntax Tree which combines language-independent AST elements with language-specific elements. For simplicity, we use the term AST in the remainder of the paper. Second, we apply the
France Dernières Nouvelles, France Actualités
Similar News:Vous pouvez également lire des articles d'actualité similaires à celui-ci que nous avons collectés auprès d'autres sources d'information.
 LICMA's Analysis of Crypto API Misuses in Python Apps: Findings and Future DirectionsExplore insights from LICMA's empirical study on crypto misuses in Python apps, highlighting the impact of user-friendly API design and of hybrid analysis.
LICMA's Analysis of Crypto API Misuses in Python Apps: Findings and Future DirectionsExplore insights from LICMA's empirical study on crypto misuses in Python apps, highlighting the impact of user-friendly API design and of hybrid analysis.
Lire la suite »
 Python Crypto API Misuses in the Wild: Analyzing Threats to ValidityLearn about the limitations in current analysis tools and frameworks, impacting the accuracy and scope of findings in crypto misuse studies.
Python Crypto API Misuses in the Wild: Analyzing Threats to ValidityLearn about the limitations in current analysis tools and frameworks, impacting the accuracy and scope of findings in crypto misuse studies.
Lire la suite »
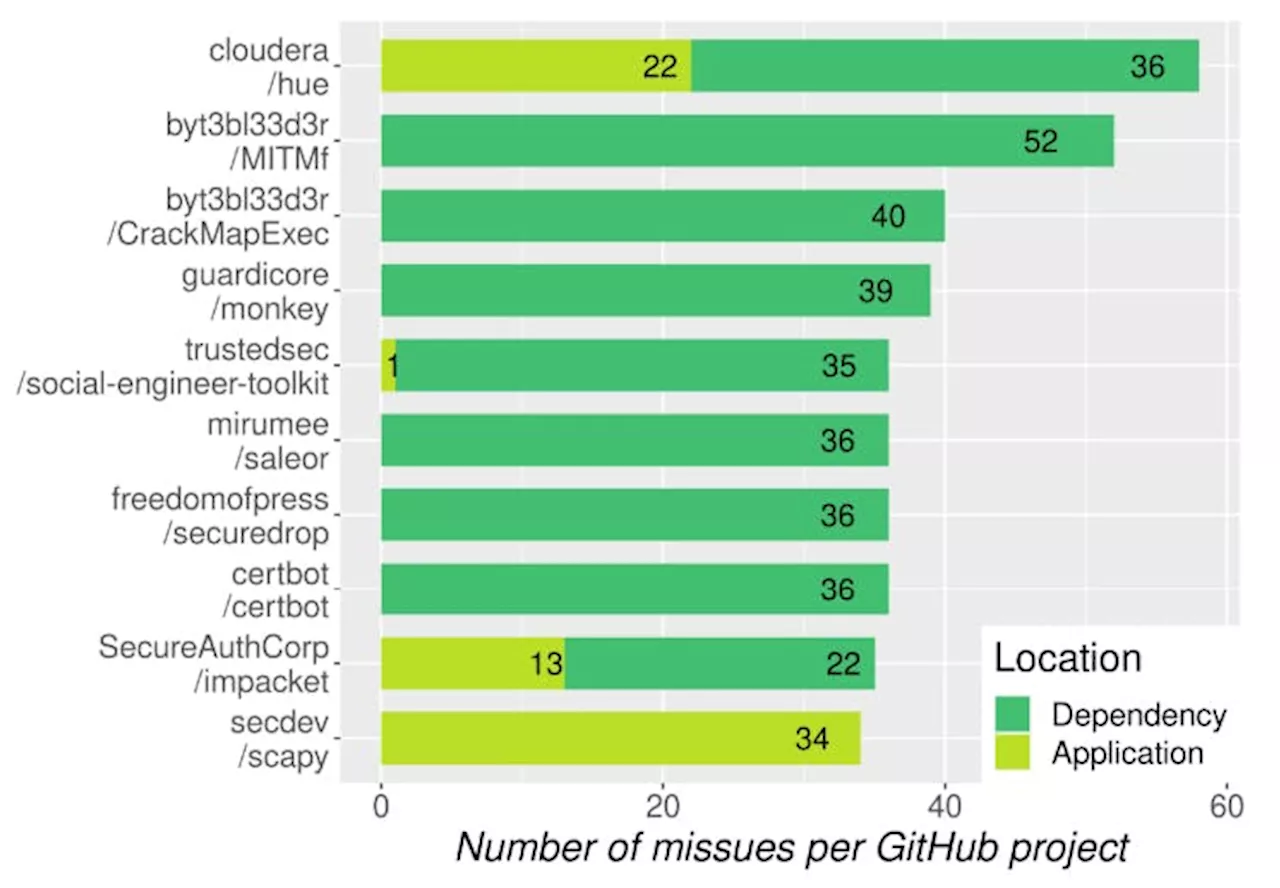 Evaluating Crypto Misuses in Python: Insights from GitHub Projects and MicroPythonLearn about definite misuses, dependency impacts, rule violations, and insights into security vulnerabilities across cryptographic libraries.
Evaluating Crypto Misuses in Python: Insights from GitHub Projects and MicroPythonLearn about definite misuses, dependency impacts, rule violations, and insights into security vulnerabilities across cryptographic libraries.
Lire la suite »
 A Comparative Analysis of Crypto API Misuses Across Programming LanguagesExplore a comparative analysis of crypto security across Python, Java, and C based on empirical studies.
A Comparative Analysis of Crypto API Misuses Across Programming LanguagesExplore a comparative analysis of crypto security across Python, Java, and C based on empirical studies.
Lire la suite »
 How We Analyzed Crypto API Misuses in 895 GitHub ProjectsDiscover the methodology behind analyzing crypto misuses in Python and MicroPython projects from GitHub and curated MicroPython repositories.
How We Analyzed Crypto API Misuses in 895 GitHub ProjectsDiscover the methodology behind analyzing crypto misuses in Python and MicroPython projects from GitHub and curated MicroPython repositories.
Lire la suite »
 Understanding Crypto API Misuse Patterns: A Comparative Study of Python, Java, and C/C++ ResultsGain insights into how API design impacts crypto misuses and discover trends in programming language security vulnerabilities.
Understanding Crypto API Misuse Patterns: A Comparative Study of Python, Java, and C/C++ ResultsGain insights into how API design impacts crypto misuses and discover trends in programming language security vulnerabilities.
Lire la suite »
